I'm working on a web application that is using Forms authentication.
<authentication mode="Forms">
<forms slidingExpiration="true"
loginUrl="~/User.aspx/LogOn"
timeout="15"
name="authToken" />
</authentication>
I'm seeing this cookie set in my browser when I log in:
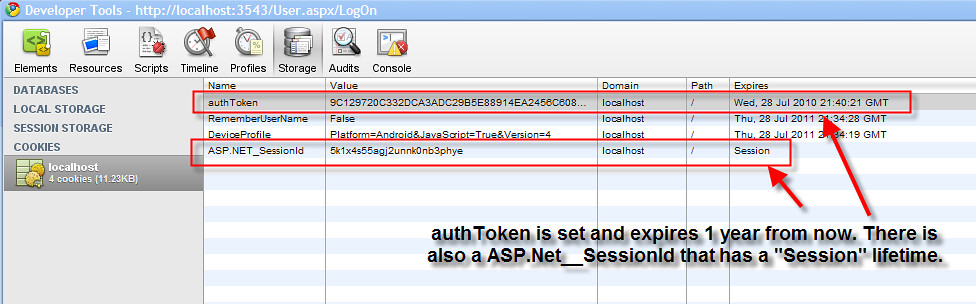
The question is what happens when I put this website in a load balanced model? Where is the ASP.net session cookie being set? I didn't explicitly do it in code, so I assume it's happening behind the scenes somewhere in ASP.Net.
Also, If the session cookie is set by web server A, I assume web server B won't recognize it and treat it as an invalid session. If this is the case, I probably don't want to use it, right?
Today I'm excited to announce built-in authentication support in Application Load Balancers (ALB). ALB can now securely authenticate users as they access applications, letting developers eliminate the code they have to write to support authentication and offload the responsibility of authentication from the backend.
Form Authentication is a token-based system. When users log in, they receive a token with user information that is stored in an encrypted cookie. When a user requests an ASP.NET page via the browser, the ASP.NET verifies whether the form authentication token is available.
Examples of login and error pages are shown in Creating the Login Form and the Error Page. Form-based authentication is not particularly secure. In form-based authentication, the content of the user dialog box is sent as plain text, and the target server is not authenticated.
You'll have to set the machine key to be the same and the name to be the same on both machines...if this is done you should have no problems load balancing with forms auth.
<authentication mode="Forms">
<forms loginUrl="~/Login/Index" defaultUrl="~/"
name=".myportal"
protection="All" slidingExpiration="true" timeout="20" path="/"
requireSSL="false"></forms>
</authentication>
<machineKey validationKey="534766AC57A2A2F6A71E6F0757A6DFF55526F7D30A467A5CDE102D0B50E0B58D613C12E27E7E778D137058E" decryptionKey="7059303602C4B0B3459A20F9CB631" decryption="Auto" validation="SHA1"/>
Sessions can get slightly more complicated. You can store the ASP.Net session state in the database or use a shared session provider to make it available for load balancing as well.
Here is a good article on storing session state in the DB: http://idunno.org/articles/277.aspx
If you love us? You can donate to us via Paypal or buy me a coffee so we can maintain and grow! Thank you!
Donate Us With